Let's start from basic: What's is AWS IAM?
AWS Identity and Access Management (IAM) is a web service that helps you securely control access to AWS resources. You use IAM to control who is authenticated (signed in) and authorized (has permissions) to use resources.
What does exactly IAM provide:
- Shared access to your AWS account
- Granular permissions
- Secure access to AWS resources for applications that run on Amazon EC2
- Multi-factor authentication (MFA)
- Identity federation
- Identity information for assurance
- PCI DSS Compliance (debatable, IMHO)
- Integrated with many AWS services
- Eventually Consistent
- Free to use
Not exactly: Here the list:
IAM currently supports the following authorization models:
- Role-based access control (RBAC). RBAC defines permissions based on a person's job function, known outside of AWS as a role.
- Attribute-based access control (ABAC) is an authorization strategy that defines permissions based on attributes. In AWS, these attributes are called tags. Tags can be attached to IAM principals (users or roles) and to AWS resources.
AWS IAM principals:
- User
- Roles
- Groups
IAM Policies:
Shared responsibilities in case of policies:
- YOU -> Define policy
- AWS -> Evaluates policy and enforce access
Policy types:
- Managed policies
- AWS managed policy
- Customer managed policy
- Inline policies
- S3, KMS, etc
- IAM:
- The IAM service supports only one type of resource-based policy called a role trust policy, which is attached to an IAM role. An IAM role is both an identity and a resource that supports resource-based policies. For that reason, you must attach both a trust policy and an identity-based policy to an IAM role. Trust policies define which principal entities (accounts, users, roles, and federated users) can assume the role.
Access control lists (ACLs) are service policies that allow you to control which principals in another account can access a resource. ACLs cannot be used to control access for a principal within the same account.
Session policies (STS): A session policy is an inline permissions policy that users pass in the session when they assume the role. You can pass the policy yourself, or you can configure your broker to insert the policy when your identities federate into AWS (if you have an identity broker configured in your environment).
How the policy structured?
- Identity-based policies: Principal is not required ( and can't be used at all), as we always attach the policy to the particular principal.
- Resource-based policies: Resource is not required (but could be provided), as the resource to which the action applies, is the resource to which the policy is attached.
- Service control policies (SCPs): Principal is not required ( and can't be used at all), but could be specified using condition (and in several different ways: StringLike: aws:PrincipalArn, aws:PrincipalAccount, and even like ArnNotLike: aws:PrincipalARN)
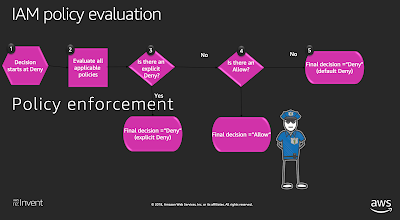
Policy evaluation process:
- Actions (or operations) – The actions or operations that the principal wants to perform.
- Resources – The AWS resource object upon which the actions or operations are performed.
- Principal – The user, role, federated user, or application that sent the request. Information about the principal includes the policies that are associated with that principal.
- Environment data – Information about the IP address, user agent, SSL enabled status, or the time of day.
- Resource data – Data related to the resource that is being requested. This can include information such as a DynamoDB table name or a tag on an Amazon EC2 instance.
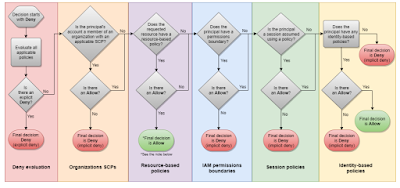
2 Main cases of the policy evaluation process:
Single account:
Cross-account:
SCP:
Session policy (STS)
Various policies and Root user:
- You cannot attach identity-based policies to the root user
- You cannot set the permissions boundary for the root user.
- You can specify the root user as the principal in a resource-based policy or an ACL.
- Resource-based policies do not affect Root user. (If you mistakenly locked your bucket(or KMS) with Deny *, you can use root user to regain control over this bucket)
- As a member of an account, the root user is affected by any SCPs for the account.
Known security issues and best practices:
Identity-based policies:
Managed policies:
- AWS regularly makes mistakes in the managed policy that could even lead to the privilege escalations:
- AWS adds and removes permissions on it will, causing either potential outage (unexpected lack of permission) or violation of the least permission principle (extra permissions that were not expected)
- A user/role allowed to add its own account to an Admin group
- A user/role allowed to create a new API key for a more privileged user account
- A user/role allowed to update the account password for a more privileged user account
- A user/role allowed to assume a privileged role directly
- iam:CreatePolicyVersion
- iam:SetDefaultPolicyVersion
- iam:AttachUserPolicy
- iam:AttachGroupPolicy
- iam:AttachRolePolicy
- iam:PutUserPolicy
- iam:PutGroupPolicy
- iam:PutRolePolicy
Inline policies:
Resource-based policies:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:Get*",
"s3:List*"
],
"Resource": "*"
}
]
}{ "Version": "2012-10-17", "Id": ProtectSensitiveBucket", "Statement": [{ "Sid": "AllowCICDOnly", "Effect": "Allow", "Principal": { "AWS": [ "arn:aws:iam::12345678:role/jenkins-prod" ] }, "Action": [ "s3:GetObject", "s3:PutObject", "s3:PutObjectACL ], "Resource": [ "arn:aws:s3:::generated-gift-cards", "arn:aws:s3:::generated-gift-cards/*", ] }]
},{
"Sid": "DenyOthers",
"Effect": "Deny",
"Principal": "*",
"Action": "s3:*",
"Resource": [
"arn:aws:s3:::generated-gift-cards",
"arn:aws:s3:::generated-gift-cards/*"
],
"Condition": {
"ArnNotEquals": {
"aws:PrincipalArn": [
"arn:aws:iam::12345678:role/jenkins-prod"
]
}
}
}
]
}IAM (trust policy)
IAM permissions boundaries:
ABAC or Tag-based controls:
- Tags becoming the Key to the whole AWS kingdom.
- The ability to create/manage tags must be extremely well enforced and controlled.
- Not all AWS services support Tags (limited scope of usage)
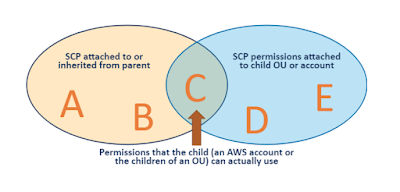
Service control policies (SCPs)
- Conditions could be used only in the DENY statements. Details here.
- Always remember about spelling mistakes in the IAM action names.
- You can't attach more than 5 SCP policies to the OU/Account (Hard limit)
- Policy size must be 5120 bytes max, including spaces. (Hard limit)
Access control lists (ACLs)
- Authenticated Users group: represents all AWS accounts. Access permission to this group allows any AWS account to access the resource
- All Users group: Access permission to this group allows anyone in the world access to the resource. The requests can be signed (authenticated) or unsigned (anonymous)






















No comments:
Post a Comment