For run Security Operation Center in your company you must create process, write procedures, hire a staff , etc. All these steps well described in thousand documents.
But what about technical components of SOC?
1. Video wall
Sure thing you need it for security events visibility. It could be LCD, Plasma or just a projector.
Usually you have more than 5 different security management programs (1-2 SIEMs, IDS management, system logs , etc) , so, you need method to show all these on display. You can't tile one display with all these windows - lack of resolution for huge amount of information.
, etc) , so, you need method to show all these on display. You can't tile one display with all these windows - lack of resolution for huge amount of information.
 , etc) , so, you need method to show all these on display. You can't tile one display with all these windows - lack of resolution for huge amount of information.
, etc) , so, you need method to show all these on display. You can't tile one display with all these windows - lack of resolution for huge amount of information.
I recommend to use very simple vb script ,created by friend of mine Roma Lazaruk, to switch between programs.
//JScript
var WshShell = WScript.CreateObject("WScript.Shell");
KL = true;
while (KL) {
WshShell.AppActivate(388);
WScript.Sleep(90000);
WshShell.AppActivate("2752");
WScript.Sleep(90000);
WshShell.AppActivate("3612");
WScript.Sleep(90000);
if (WshShell.AppActivate("notepad")) {
WriteWord();
KL = false;
}
}
It gives you possibility to see and read all security information on video wall and adjust visibility interval between programs. This script use PID numbers (for switching between different process with the same name like browser windows ) for program activation and you must run notepad.exe to kill the script.
2. Knowledge base.
Sharing knowledge between teem players save your time, increase team productivity and secure you from personnel turnover problem.
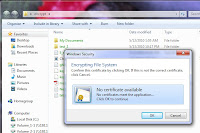
Sure thing the best engine for knowledge base is Wiki. More over you can create really secure knowledge base based on mutual ssl authentication with certificates on smart card and wiki single sign on (SSO) by user cn. For your convenience Andrey Dugin write a wonderful article about this!