Now service:
- Does full port and vulnerability scan of the caller's IP
- Immediately perform and return tcp scan results. Starts vulnerability scan in background.
- Visit nmap.me again in about 30min(depends on load), and results of the vulnerability scan (port, service, vulnerability, CVE) for you IP will be displayed.
- You can use, console friendly endpoint : scan.nmap.me , or
- use a human readable website: nmap.me
Good scan results:
Not so good scan results:
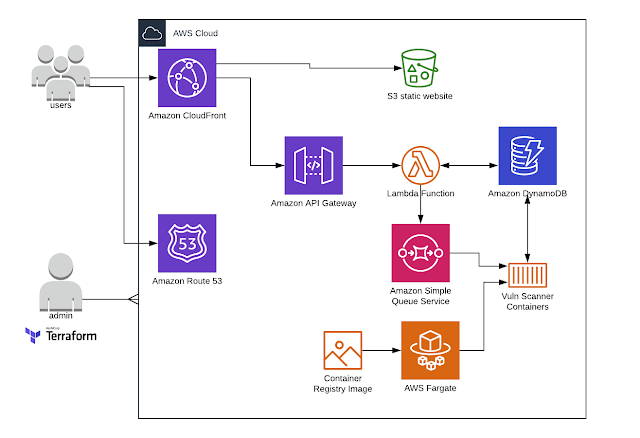
As previously service is built using AWS native capabilities, serverless and containerized approach and design to be extremely scalable.
Quick FAQ:
What's new? Now it does full vulnerability scan of the IP.
What it does? Scan your external IP for open TCP ports and known vulnerabilities.
How to use? Simply do _curl scan.nmap.me_ from your console/terminal or open this webite in browser. You will get TCP scan results immediately and you will need to visit same page in an hour to get vulnerability scan results.
What it's scanning for?: Uses nmap NSE script to perform scan for known vulnerabilities. Based on https://github.com/vulnersCom/nmap-vulners
How fast? Whole TCP scan takes about a few second and results are immediately shown. After this vuln scan is starting. Depending of the backend load it might take about an hour to get scanned. After this simply visit the same page again to get vulnerability scan results. Scan results for each requester IP are cached for 1 hour (TCP scan) and 24 hours (Vuln scan) to reduce load and prevent abuse.


No comments:
Post a Comment