Let's talk about smart card and file encryption. Your company or just you got a smart card. You would like to use it in stand alone computer scheme (domain infrastructure gives you a lot more features). For this purpose from my point of view you have two best solutions:
1-st - Use a wonderful and powerful tool called TrueCrypt, which has been recommended by Bruce Schneier
As first step you must point TrueCrypt to PKCS 11 library (usually you got it from vendor)
Note: in 64 platform you must point to x86 dlls.
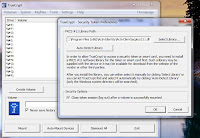 Second step is to go to a Settings/key files and chose Add Token Files option.
Second step is to go to a Settings/key files and chose Add Token Files option.
You gonna be asked for a PIN to your smart card (it must be already inserted)
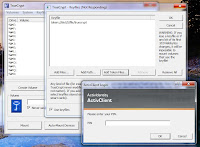 If you don't have this key file yet (which is normal for first use of smart card) you should generate it as a next step of pressing " import new key file"
If you don't have this key file yet (which is normal for first use of smart card) you should generate it as a next step of pressing " import new key file"
-start TrueCrypt at the background
-enable all auto dismount options and set idle time-out to 20 min.
-enable wipe cache option for extra security
Note: do not enable auto mount option - it requires password even in case of key file usage.
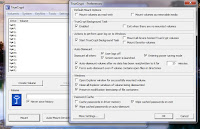 For user convenience add encrypted disk to favorites and assign hot keys for mount and unmount this disk.
For user convenience add encrypted disk to favorites and assign hot keys for mount and unmount this disk.
1. True Crypt creates key file and stores it on smart card file system as a files protected by PIN. It means that spyware can withdraw this key file from smart in background card if user provide PIN for it. (I haven't seen such program yet but it's possible to do such key and pin "fishing" attack )
2.User must mount disk before use and unmount after.
3. If user lose smart card it's impossible to restore data. But, there is a solution for this: security officer could use a second smart card for storing copy of user encryption key file and keep this backup card (like miniHSM) in safe place.
2-nd Solution have been provided to you by Microsoft for free (there's no such thing as a free lunch :-)) ) in Windows Vista and Windows 7.
Both of these operation systems support using smart card for EFS file encryption out of box.
(There is a possibility to use such feature in Windows XP but only in domain configuration with smart card logon)
Before enable it you must some-how generate and import certificate to your smart card.
I use for this purpose a nice CA based on open-ssl. (This CA with a lot of features has been developed by friend of mine Gorthaur and I hope he will write a nice article about it soon)
First step is choosing your certificate for future file encryption
You will see it when you take out the card from reader. You could decrypt and encrypt your files even without smart card and even after lock/unlock PC. I'm dead sure that it's absolutely insecure!
So, let's add more security! Type gpedit.msc and go to Encryption file system properties.
Here we have two main option:
-use cashing capable symmetric key (A symmetric key is derived from the user’s private key and cached in protected memory) It gives you more performance and you don't need to keep smart card in reader all the time.
-use a non-cached mode. It require to keep smart card in reader all the time.
I prefer cached mode with short time caching (5 min) (windows default is 480 min!!!!) and clearing a cache when user lock the station. I think it good compromise between performance and security.
If you try to write to encrypted area without smart card inserted (and when key cache period expired) you will got messages below
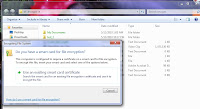
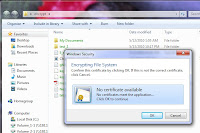 This message you will got if you will try to read files in encrypted area without smart card and after cached key expired:
This message you will got if you will try to read files in encrypted area without smart card and after cached key expired: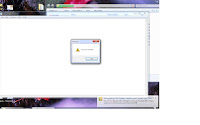 Do not forget to type PIN when you insert smart card back! PIN request window is located at the system notification area and it's really small. Do not miss it !
Do not forget to type PIN when you insert smart card back! PIN request window is located at the system notification area and it's really small. Do not miss it !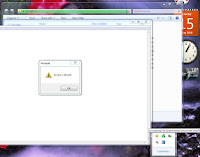
That's all rookies. Stay secured!







No comments:
Post a Comment